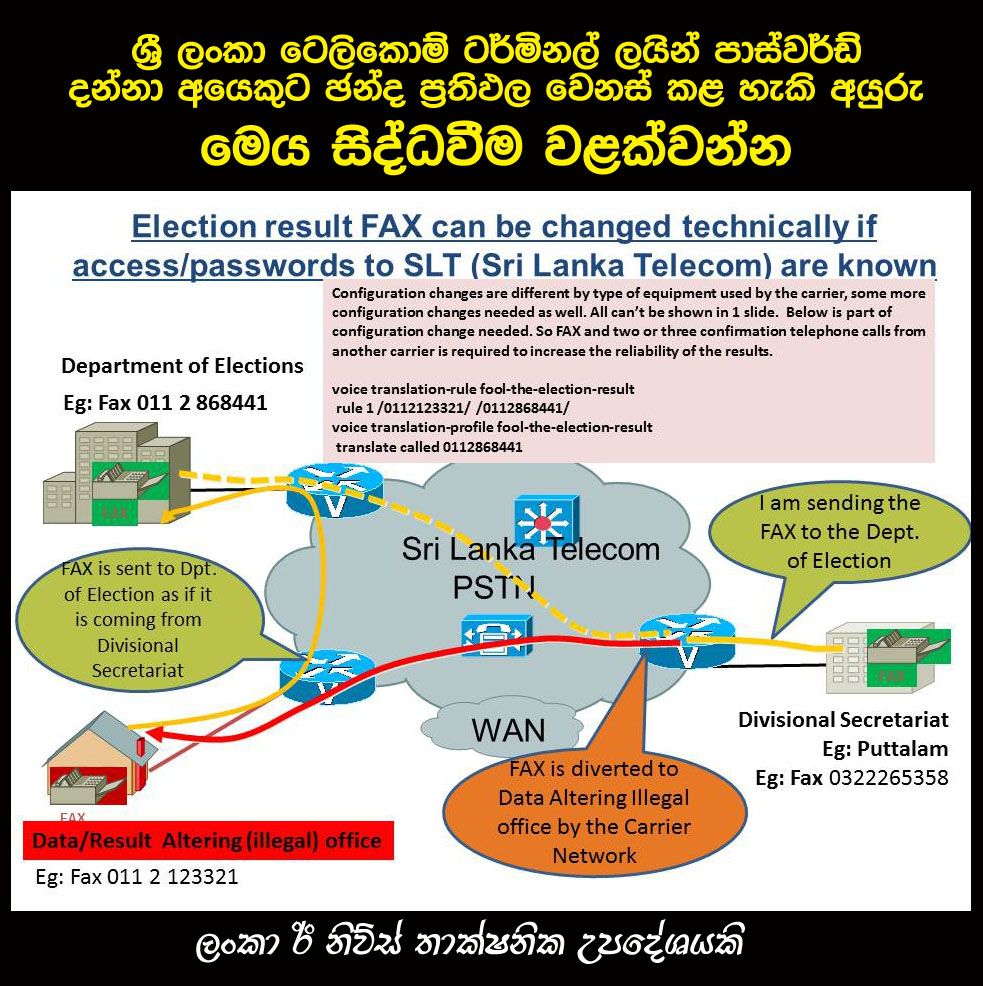
(ලංකා ඊ නිව්ස් -2015.ජන.04, ප.ව.7.15) පහත ඇති රූපය විශාල කර බලන්න
---------------------------
by (2015-01-04 17:41:49)
Leave a Reply
Wishesha Authentication system ekak daanna ona saha VPN eka athule yana ewa encrypt karala yawana ona
-- by Linux Man on 2015-01-04
DO NOT PUBLISH-CONFIDENTIAL.............
These are the views of election that we are receiving (international views) My3 will win the election, but definitely MARA will come into the power by threatening MACO, Military invade. And he has been spreading this rumor saying what ever voters do he will be the president. he is using Gobase theory. Change this attitude some how, otherwise voters will get fear of voting towards MY3, and they will give up casting there votes. Some how give a impression that MARA will loose and he will run away from SL.
-- by balaya on 2015-01-04
I think this is possible scenario. In data communication, we called these kinds of attacks as Man in the Middle attacks (MitM). For faxes, i don't think its require passwords. People in the carrier network can reroute traffic by altering some configuration in the carrier network. Illegal office will be working as a relay office to election office. This is very much easy to deploy since they know all incoming faxes and every single fax will go to a specific location. The best solution is, maintain parallel collecting center apart from government process, by using alternative communication media.
The best way is use satellite phones and fax machines. e.g. Inmartsat-Fleet Broadband 150 (this device will give satellite based fax services). However, This will be costly and logistic will be very hard
Easy way is, use Skype. You need laptop, scanner and internet connection (USB dongle). Since traffic is encrypted, they will not able to alter. Since number of subscribers is high, it is not able to trace a single communication.
Next once is use Google drive or any FTP site to upload data (google drive is using SSL traffics, so we believe it is hard to break).
However, these are my suggestions
-- by Harshana Kavshalya on 2015-01-04
If the Department of Elections can call the divisional secretariat after receiving the fax from them to verify the contents of the fax before announcing the results, this problem can be resolved.
-- by Vijitha on 2015-01-05
Not for fax transmission but for online document transmission there is a way to send documents securely by using data encryption keys downloadable through the internet.
Symantec, Commodo, VeriSign, PGP, Public and Private Keys etc. are the technical jargon involved in this regard.
By making an online payment through credit card to those institutions providing secure data encryption and transmission services one can download Public and Private Keys to encrypt the files that are sent through electronic means.
For example 26 pairs of keys are bought to be used at 25 counting centers and Colombo Main Election Office (CEO). One pair of keys are used at CEO and the balance 25 keys each are used at each counting office to encrypt the documents containing the election results. Each document is encrypted by both Public and Private Key before being sent through the wires/wireless. Such an encrypted document cannot be tampered even though intercepted on the way because the decryption needs the other pair of Keys which are at the main election office.
The decryption machine at CEO must be operated by an impartial officer because if he sends the keys to government backed hackers they would extract and alter the data. Ideally this decryption machine must be firewalled, outgoing blocked, incoming limited to from counting offices, screen recording enabled throughout the election result decryption process and an external video surveillance camera installed to monitor the activities/screen of the operator.
As an alternative a PC without internet connection can be used where the incoming files are copied to a pen drive and then manually copied to the decryption machine for the rest of the process. This is very safe method for online hacking attempts. However the other measures in the previous paragraph must be followed.
Other ancillary measures involve the use of video conferencing to verify and authenticate the genuineness of transmitted figures by an already recognized officer/a team of officers and opposition members visually and audibly confirming the results so that at the CEO the government and opposition members can visually and audibly verify the results.
I request these and other measures that may be proposed by others be used to ensure the integrity of the election results.
-- by Silva on 2015-01-05
අජිත් ගලප්පත්තිගේ සිනමා විචාර එකතුව
අතීතයෙන් පාඩමක් - විශේෂඥ වෛද්ය අජිත් අමරසිංහ ලිපි